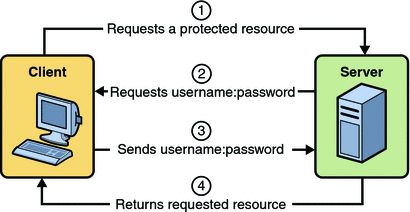
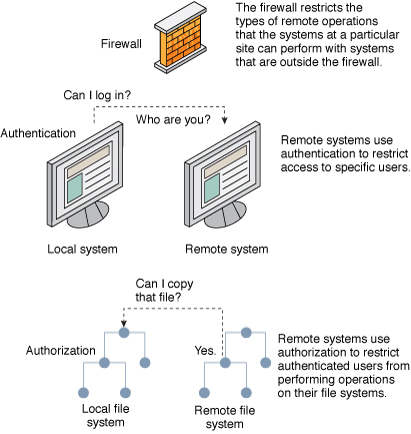
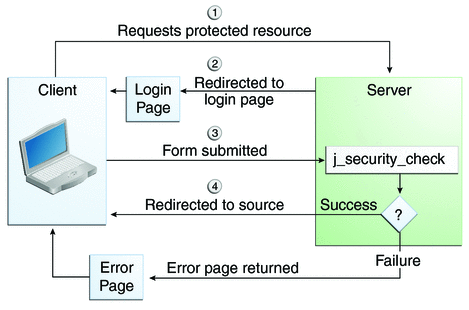
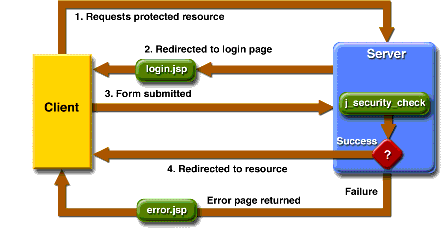
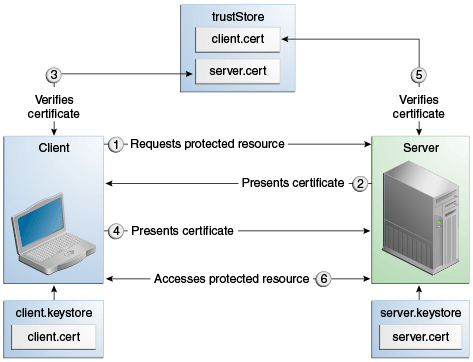
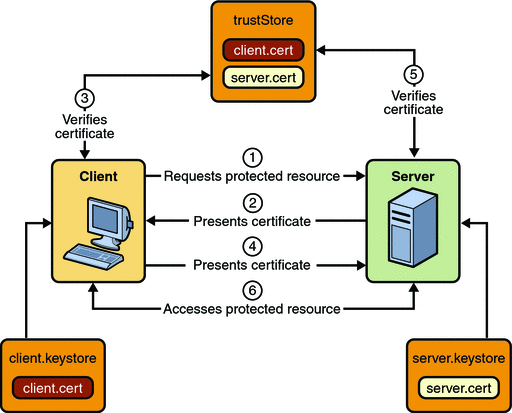
Towards the Construction of a User Unique Authentication Mechanism on LMS Platforms through Model-Driven Engineering (MDE)
![Entity Authentication Mechanism - Enterprise-Wide Security Architecture and Solutions Presentation Guide [Book] Entity Authentication Mechanism - Enterprise-Wide Security Architecture and Solutions Presentation Guide [Book]](https://www.oreilly.com/library/view/enterprise-wide-security-architecture/0738402087/bg38.png)
Entity Authentication Mechanism - Enterprise-Wide Security Architecture and Solutions Presentation Guide [Book]

Communication links associated with (a) single stage authentication... | Download Scientific Diagram
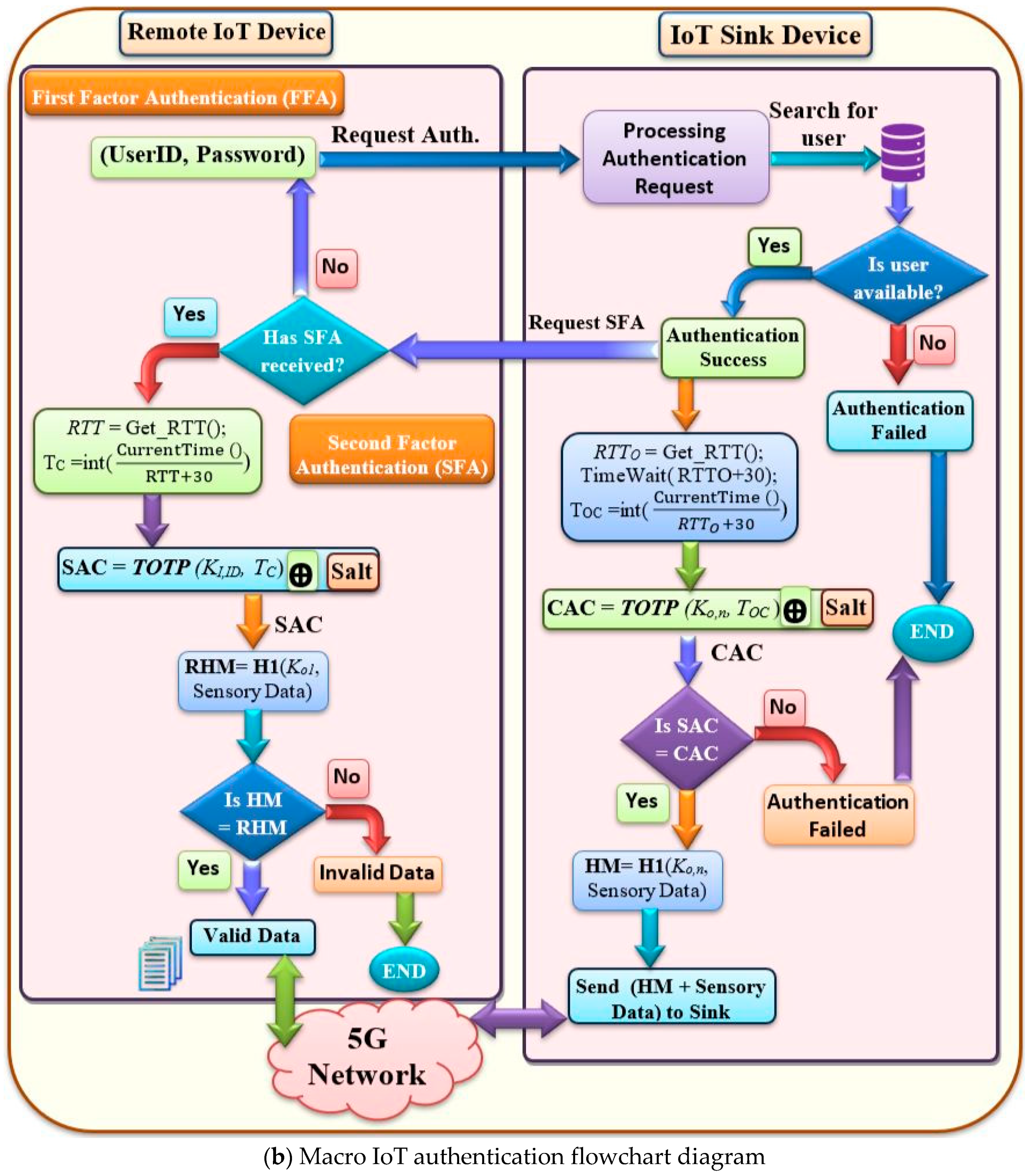
Sensors | Free Full-Text | An Effective Multifactor Authentication Mechanism Based on Combiners of Hash Function over Internet of Things | HTML
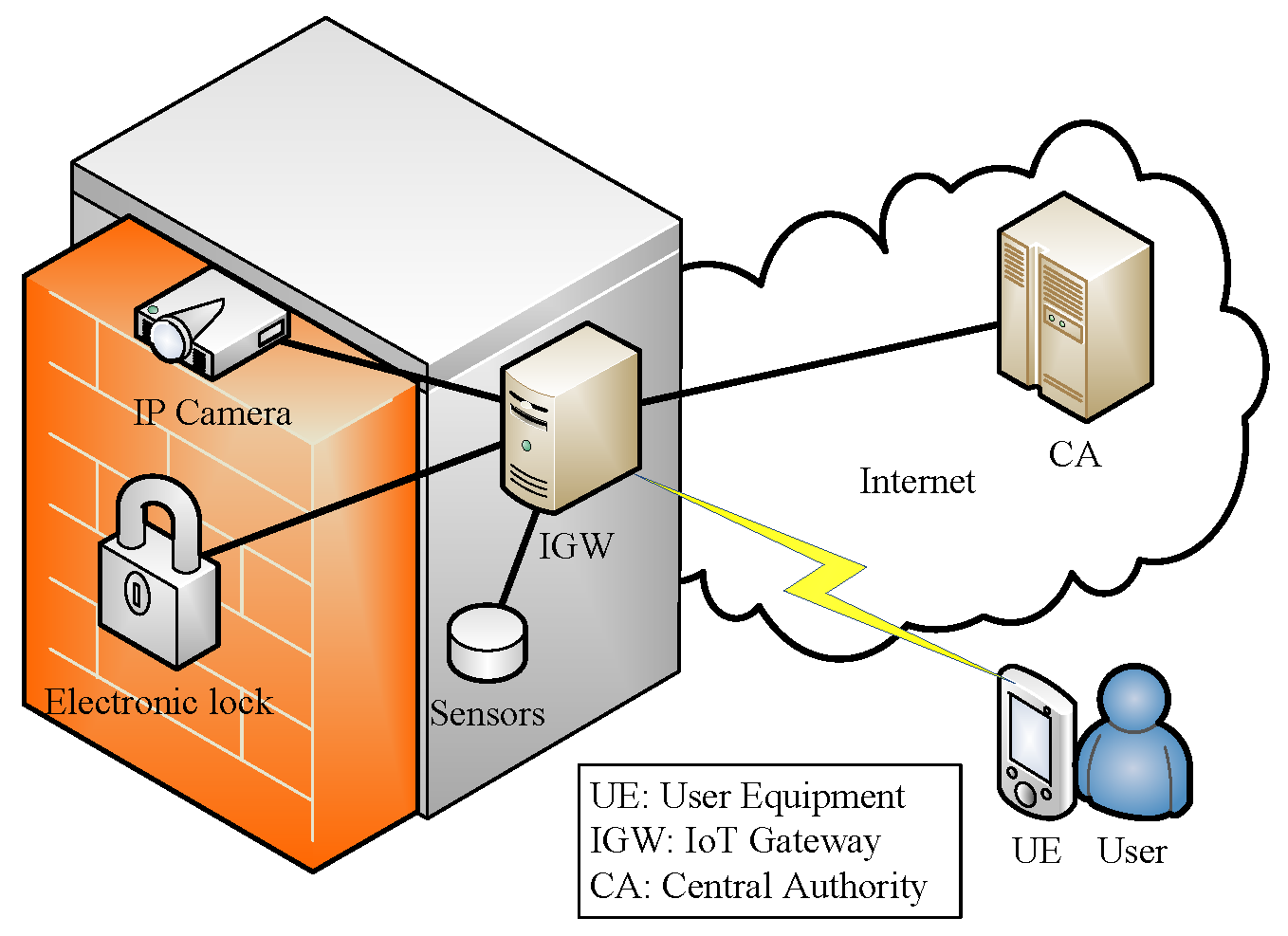
Symmetry | Free Full-Text | Geometric Authentication Mechanism for Enhancing Security in IoT Environment

Comparison of different authentication mechanisms in cloud environment. | Download Scientific Diagram
PLOS ONE: Cryptanalysis and Improvement of "A Secure Password Authentication Mechanism for Seamless Handover in Proxy Mobile IPv6 Networks"