
Security Vulnerabilities of Neural Networks | by Matthew Stewart, PhD Researcher | Towards Data Science

AutoZOOM : Background and Methods 3 . 1 Black-box Attack Formulation and Zeroth Order Optimization | Semantic Scholar

Proposed method for black-box adversarial attacks in autonomous vehicle... | Download Scientific Diagram
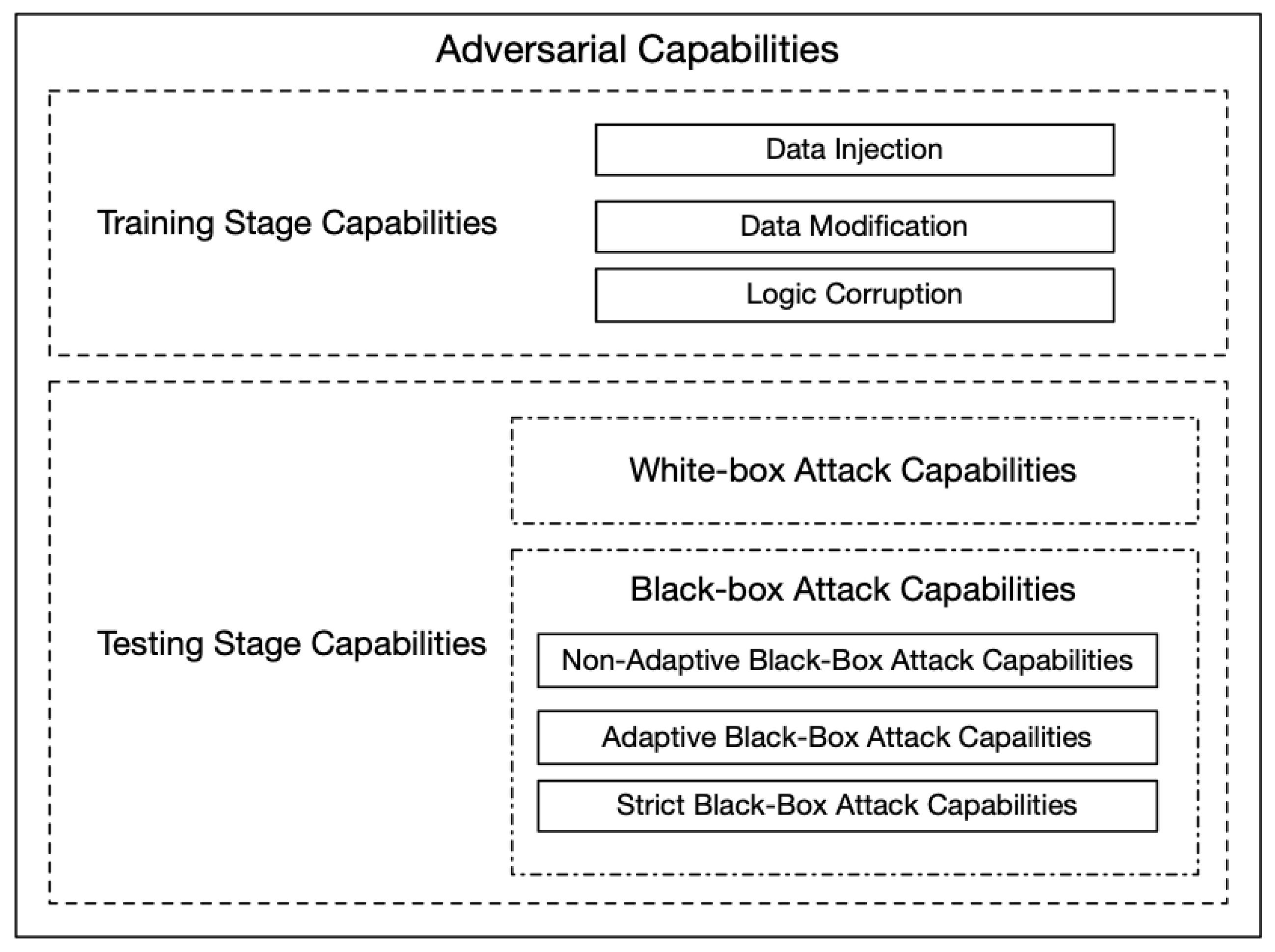
Applied Sciences | Free Full-Text | Review of Artificial Intelligence Adversarial Attack and Defense Technologies | HTML

Perceptual quality-preserving black-box attack against deep learning image classifiers - ScienceDirect

Tricking a Machine into Thinking You're Milla Jovovich | by Rey Reza Wiyatno | Element AI Lab | Medium

python - which attack in cleverhans is grey box attack and which is white/black box attack in cleverhans library? - Stack Overflow











![PDF] Black-box Adversarial Attacks in Autonomous Vehicle Technology | Semantic Scholar PDF] Black-box Adversarial Attacks in Autonomous Vehicle Technology | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b82903405c8459d13867d7c243cddb7f257df406/4-Figure2-1.png)



