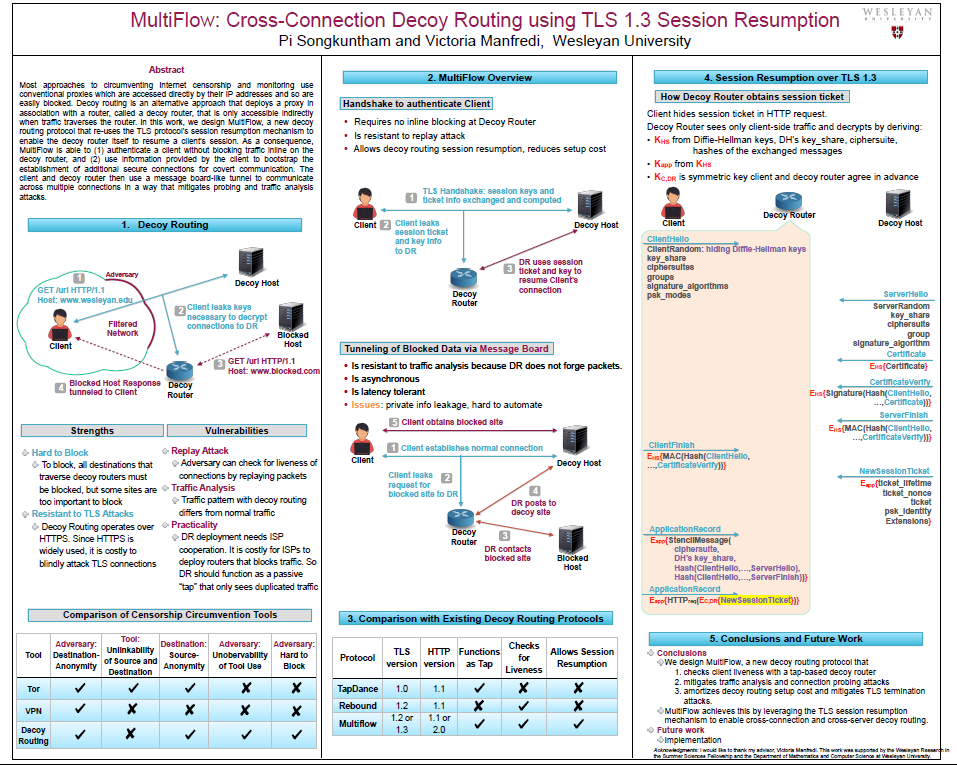
![PDF] The Waterfall of Liberty: Decoy Routing Circumvention that Resists Routing Attacks | Semantic Scholar PDF] The Waterfall of Liberty: Decoy Routing Circumvention that Resists Routing Attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6d5f3b8e7c59fc425dccc7d65b499bfbe74cd4dd/8-Figure4-1.png)
PDF] The Waterfall of Liberty: Decoy Routing Circumvention that Resists Routing Attacks | Semantic Scholar

Routing Around Decoys Max Schuchard, John Geddes, Christopher Thompson, Nicholas Hopper Proposed in FOCI'11, USINIX Security'11 and CCS'11 Presented by: - ppt download
![PDF] The Waterfall of Liberty: Decoy Routing Circumvention that Resists Routing Attacks | Semantic Scholar PDF] The Waterfall of Liberty: Decoy Routing Circumvention that Resists Routing Attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6d5f3b8e7c59fc425dccc7d65b499bfbe74cd4dd/10-Figure5-1.png)
PDF] The Waterfall of Liberty: Decoy Routing Circumvention that Resists Routing Attacks | Semantic Scholar

Decoy Routing: The user access blocked.com, through DR. To the censor... | Download Scientific Diagram