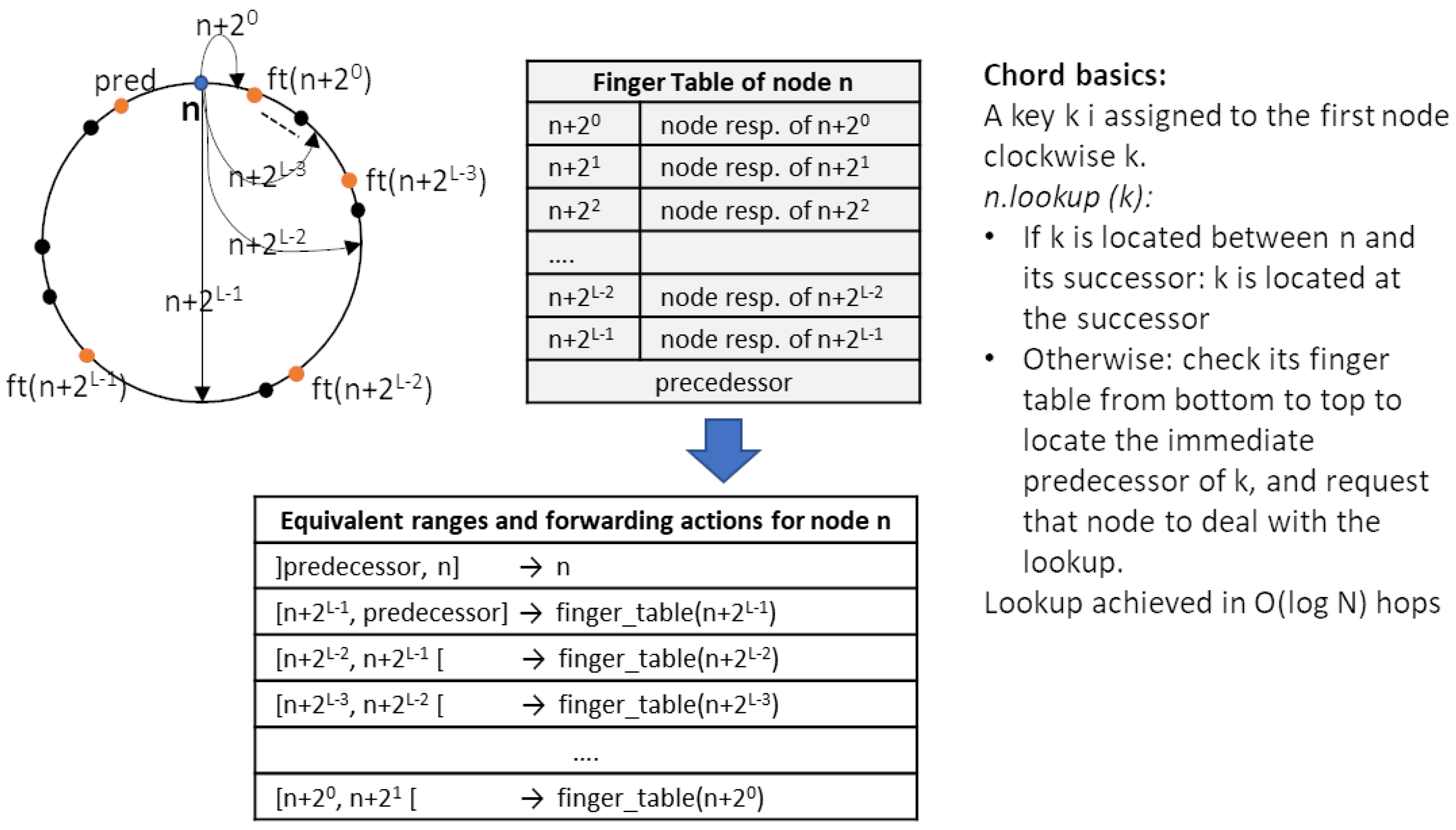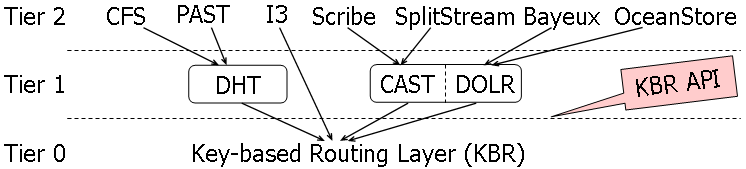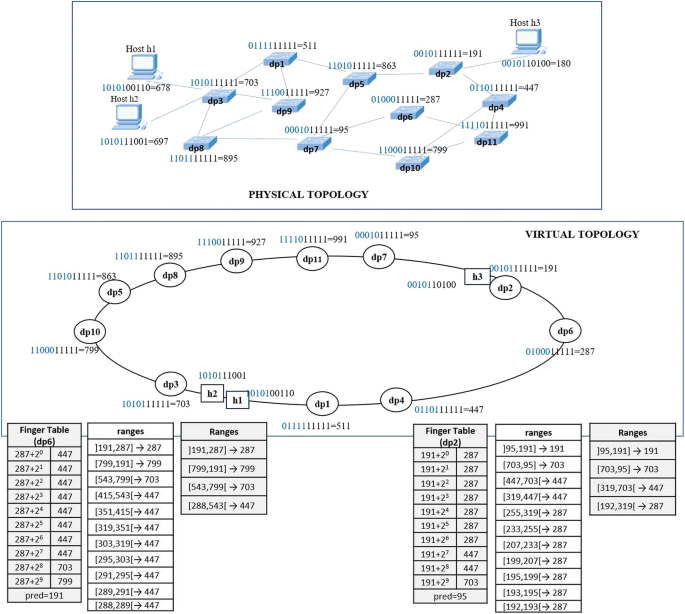
OpenFlow Compatible Key-Based Routing Protocol: Adapting SDN Networks to Content/Service-Centric Paradigm | SpringerLink

Protocols SMEER (Secure Multitier Energy Efficient Routing Protocol) and SCOR (Secure Elliptic curve based Chaotic key Galois Cryptography on Opportunistic Routing) - ScienceDirect

Firewalla on Twitter: "The magic of Policy Based Routing in Firewalla ... it is simple ... and magical :) Learn more about it in this article https://t.co/jQb5HBWQ0t on how to split traffic

KIT – University of the State of Baden-Wuerttemberg and National Research Center of the Helmholtz Association Institute of Telematics, Department of Computer. - ppt download
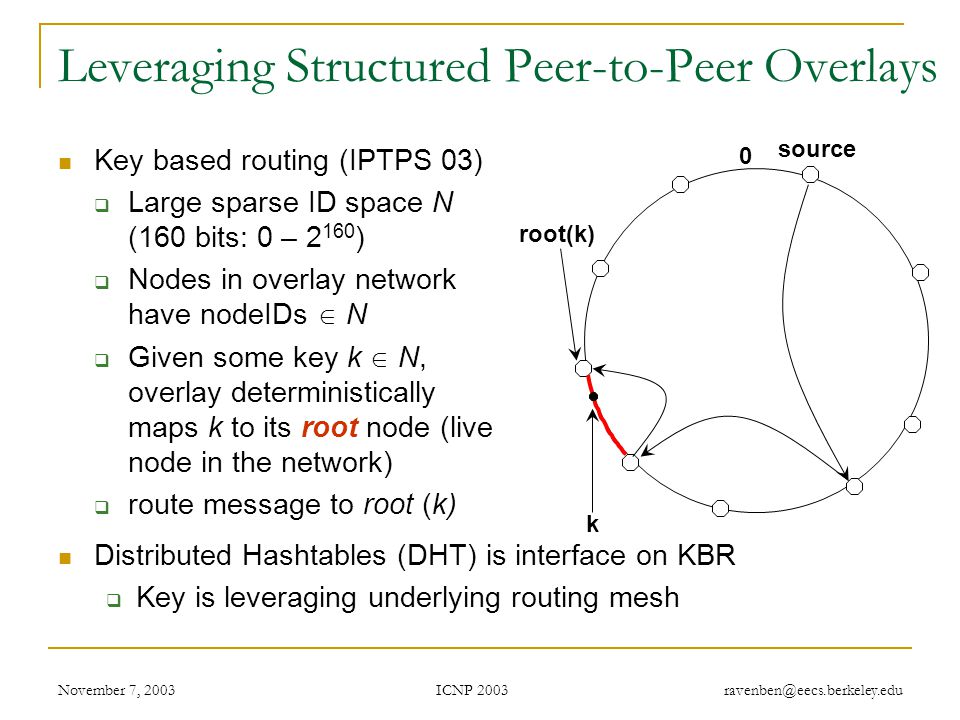



![PDF] S/Kademlia: A practicable approach towards secure key-based routing | Semantic Scholar PDF] S/Kademlia: A practicable approach towards secure key-based routing | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d22c179ffeea89d0a42c47e6c1560a7a250b25b0/2-Figure1-1.png)








![PDF] Providing Efficient Key Based Routing for Multiple Applications | Semantic Scholar PDF] Providing Efficient Key Based Routing for Multiple Applications | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/bb7c9f5e3b00979396dd307f88c658c72a03cdaf/95-Figure10.2-1.png)