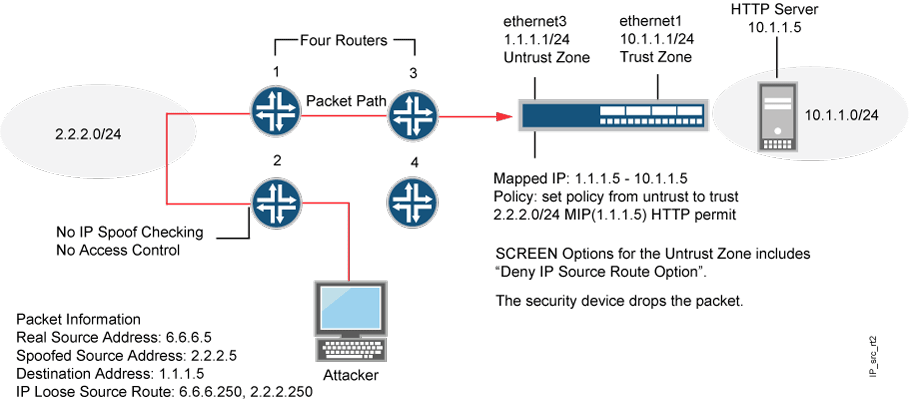
Attacker Evasion Techniques | Attack Detection and Prevention User Guide for Security Devices | Juniper Networks TechLibrary
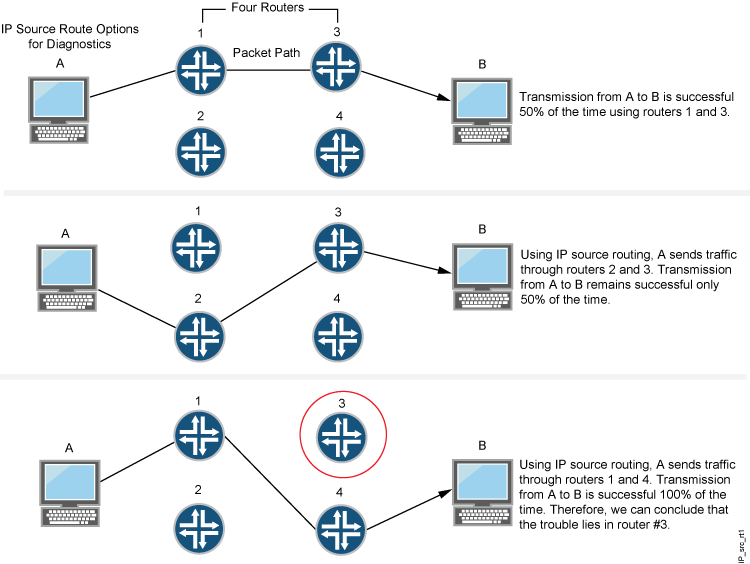
Attacker Evasion Techniques | Attack Detection and Prevention User Guide for Security Devices | Juniper Networks TechLibrary

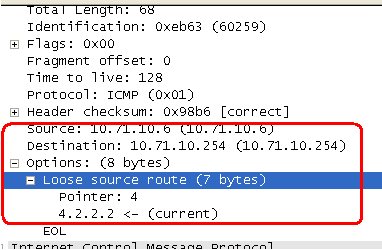
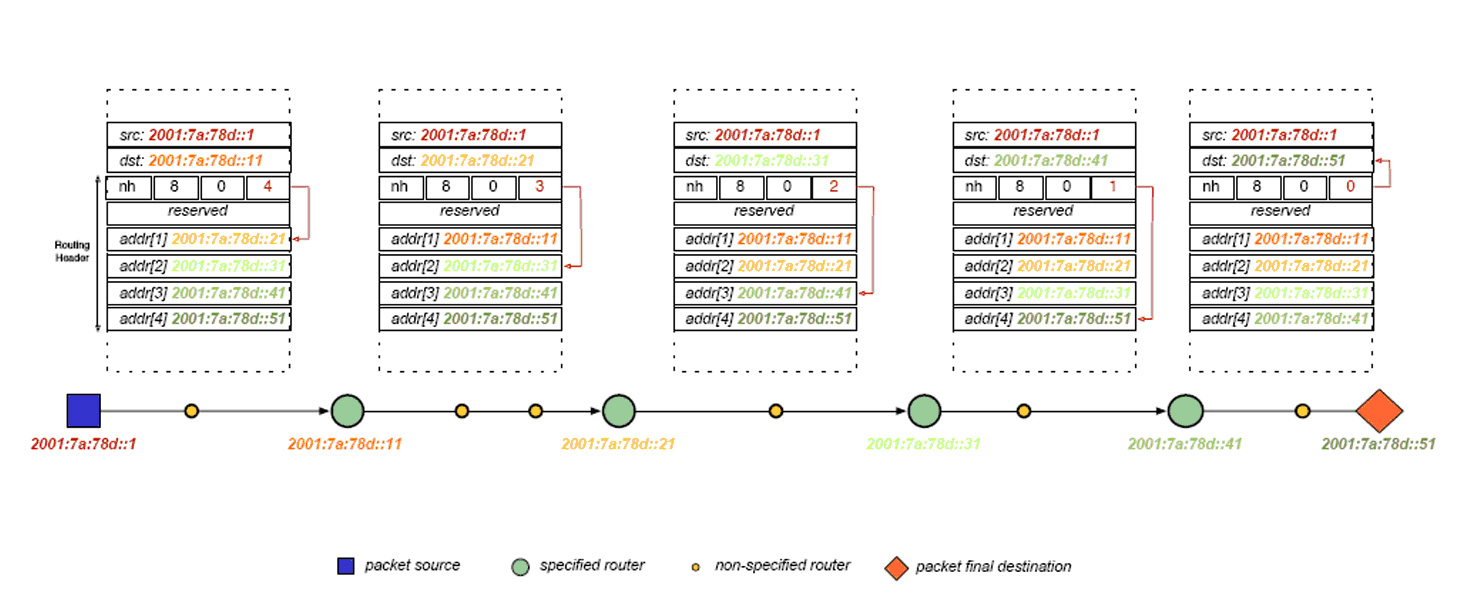
8.5 IP Source Routing Option | TCP/IP Illustrated, Vol. 1: The Protocols (Addison-Wesley Professional Computing Series)









![The IP Packet Header | Routing TCP[s]IP (Vol. 11998) The IP Packet Header | Routing TCP[s]IP (Vol. 11998)](https://flylib.com/books/2/298/1/html/2/images/1578700418/graphics/02fig06.gif)