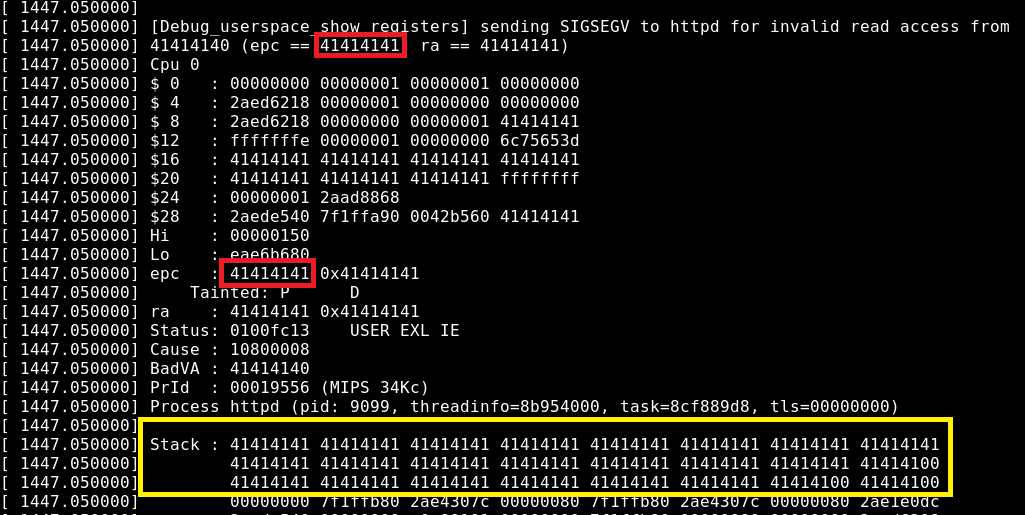
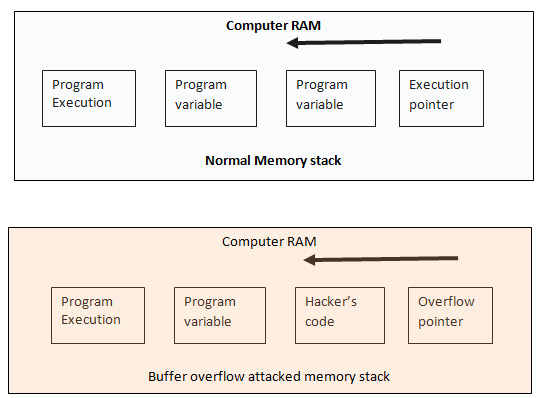
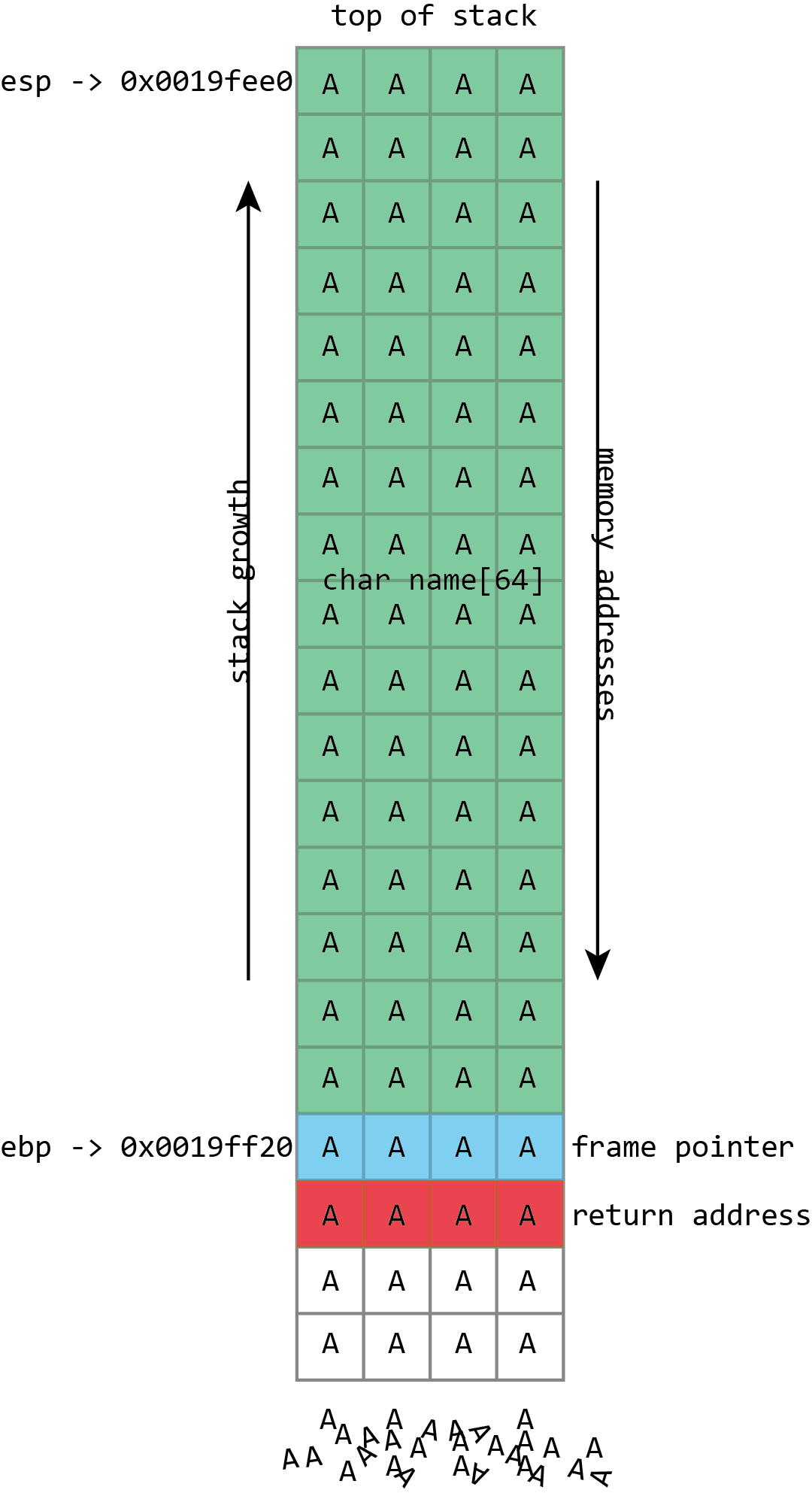
The computer buffer overflow threats, detection and prevention techniques and Intel processor C code execution environment

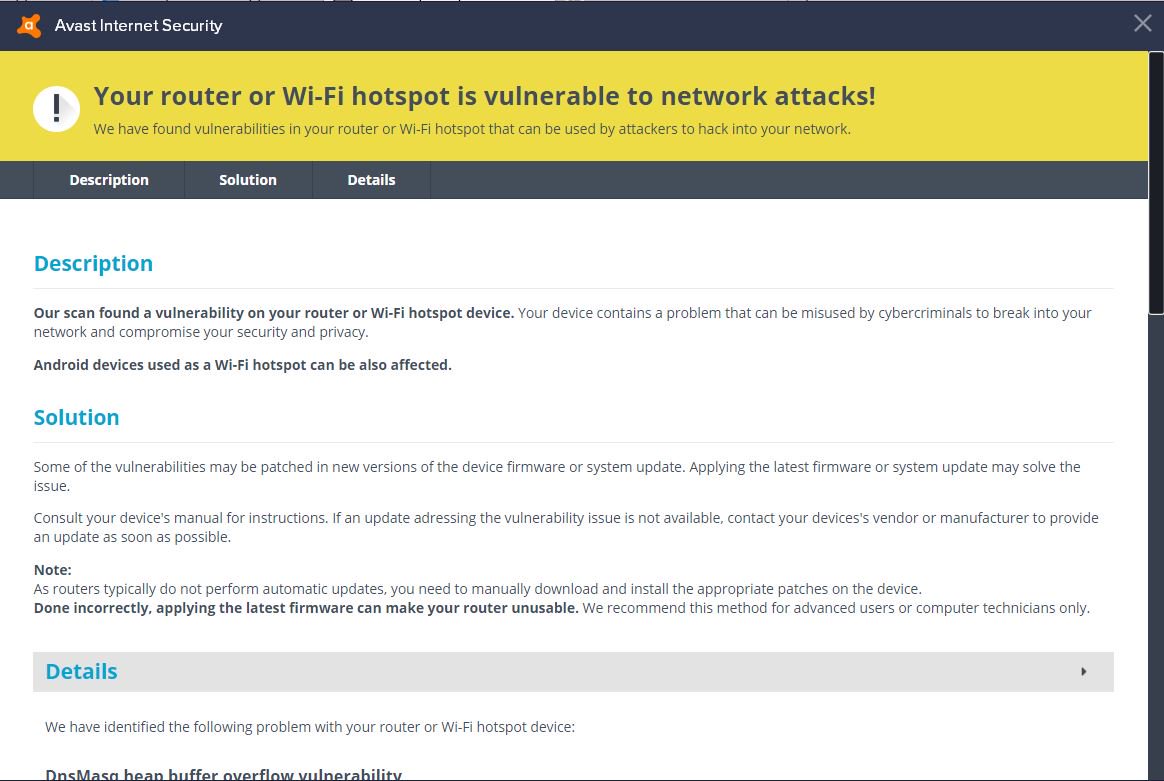
How To Fix CVE-2021-34991- A Pre-Authentication Buffer Overflow On Multiple Netgear Products? - The Sec Master
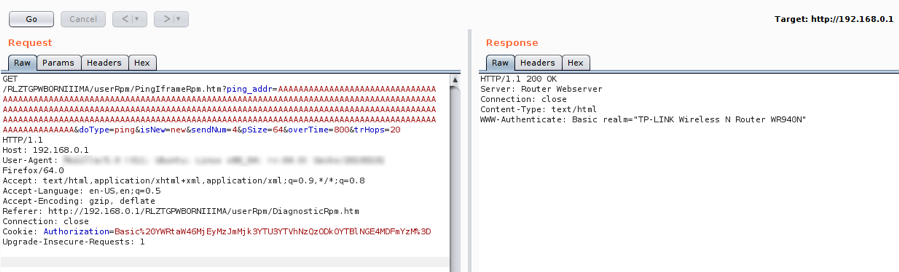
![TP-Link Wireless N Router WR840N – ARP Poisoning cause Buffer Overflow / Upgraded-ARP-Poisoning tool [CVE-2021-29280] : – HackingVila TP-Link Wireless N Router WR840N – ARP Poisoning cause Buffer Overflow / Upgraded-ARP-Poisoning tool [CVE-2021-29280] : – HackingVila](https://hackingvila.files.wordpress.com/2021/04/arp_cache_poisoning.jpg?w=1024)
TP-Link Wireless N Router WR840N – ARP Poisoning cause Buffer Overflow / Upgraded-ARP-Poisoning tool [CVE-2021-29280] : – HackingVila